(Revision 1.2, April 2023)
Product specifications and availability are subject to change without notice. Dalet is a registered trademark owned by Dalet. All other brands and trademarks are those of their respective owner.
Disclaimer
Dalet Iris is a software Network Appliance solution designed to securely interconnect multiple sites (typically Cloud and on-premises environments). Its main usage is to provide a gateway between Dalet PrivateCloud-hosted services and customer private on-premises systems whenever such a topology applies.
Customer can always (and is encouraged to) use its own existing solution to perform such a connection to leverage its existing network solutions in place. Dalet products have been tested and validated against Iris.
Dalet Iris is meant to be deployed on customer's local network, either on a bare-metal server or virtual machine.
The peer connection on Cloud-side is provided through specific Cloud provider services, e.g:
- AWS : Uses AWS Site to Site VPN or Cloud connect capability.
Presentation
General
Dalet Iris is a software network gateway solution that aims to provide site-to-site connectivity, able to interconnect a Cloud provider with an on-premises solution.
Interconnection can be done through multiple means, such as:
- "Cloud-Connect" with a provider: Iris will act as a Router and Firewall.
- VPN tunnel (IPSEC) with a provider: Iris will act as IPSEC, Router and Firewall.
It is composed of 1 (2 for High-Availability) Ubuntu Linux servers sharing a VIP (virtual IP address) to provide high availability.
It provides the below services:
- Core network services:
- Router (static, BGP, OSPF)
- Firewall
- IPSEC VPN (when connection through IPSEC)
- Connectivity services (optional)
- DNS
- DHCP
- OpenVPN
- Wireguard
Open Source embedded components
Iris integrates the below open-source components to operate the service:
- Core opensource components
- Stronsgwan (IPSEC protocol implementation - when connection through IPSEC)
- FRR (network router, implements Static, BGP & OSPF routing protocols)
- NFTables (firewalling & NAT service)
- Optional feature (deployed on specific requirements)
- Keepalived (VRRP protocol implementation)
- OpenVPN (remote access, can also be used to setup a tunnel instead of using IPSEC)
- Kea (DHCP related services whenever needed)
- PowerDNS (DNS related services whenever needed)
- WireGuard (remote access, can also be used to setup a tunnel instead of using IPSEC)
It also includes all the underlying components (OpenSSL, ...) and is based on an Ubuntu LTS Linux distribution.
Team in charge
The Dalet CSOps team is in charge of deploying & maintaining Iris solution.
Restrictions
Iris is NOT compatible with docker or Kubernetes and cannot be deployed on those servers as it uses NFTABLES rather than IPTABLES firewall. It must run on "legacy" dedicated Linux Operating System and server.
Implementation diagram
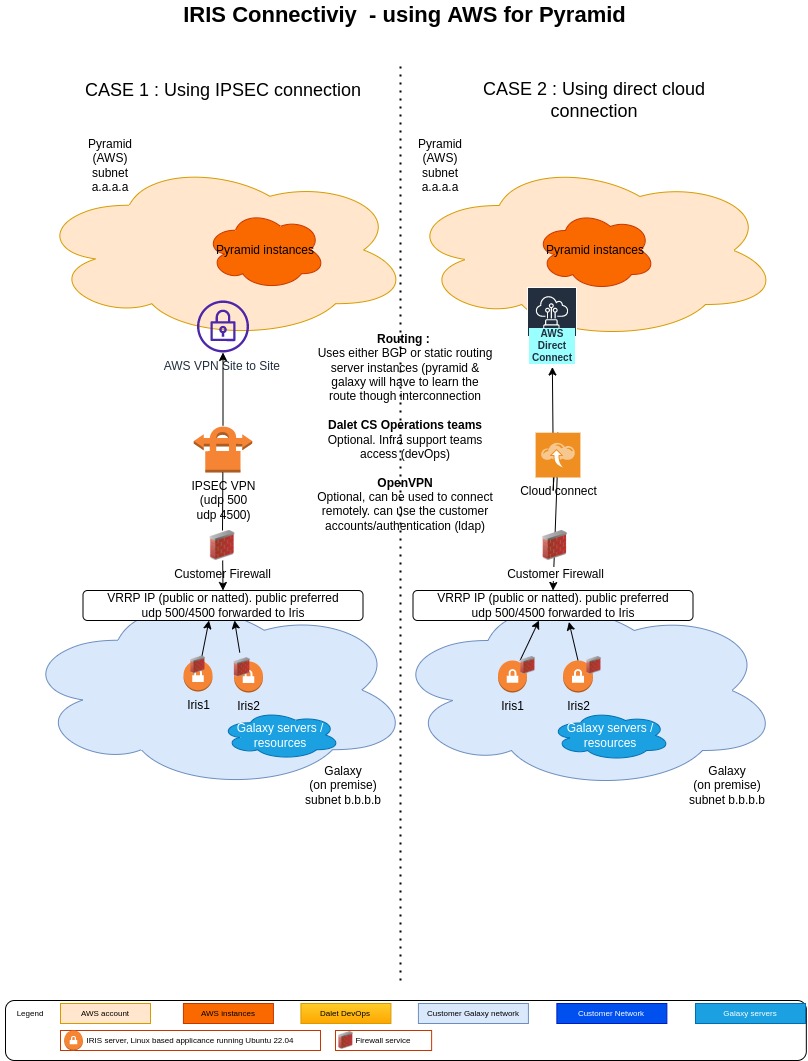
Two implementations are expected:
- Interconnect solution using a VPN tunnel like IPSEC
- Interconnect through a Cloud Connect solution
Implementation Requirements
Dalet Iris acting as a router, it will send traffic between 2 locations using a restricted list of protocols, list is provided in the below diagram.
Subnets must be known and shared by both Pyramid & Galaxy to setup IPSEC connection (when using IPSEC) and the routing. This can also extend to external services like Active Directory (possibly behind a DMZ).
Related to routing:
- The galaxy servers will need to have a route defined to reach the pyramid servers. This can be done by the customer network team or on the galaxy server themselves in the case Iris servers are located in the same subnet than Galaxy ones.
- The Pyramid servers will need to have a route defined to reach out the Galaxy services. This will be implemented by Dalet CSOps as part of the service deployment.
- Any other component like corporate Active Directory access will need to have a route to be accessed by Pyramid servers.
- DNS resolution might need to be added on customer DNS to resolve pyramid instances whenever the DNS entries are not public.
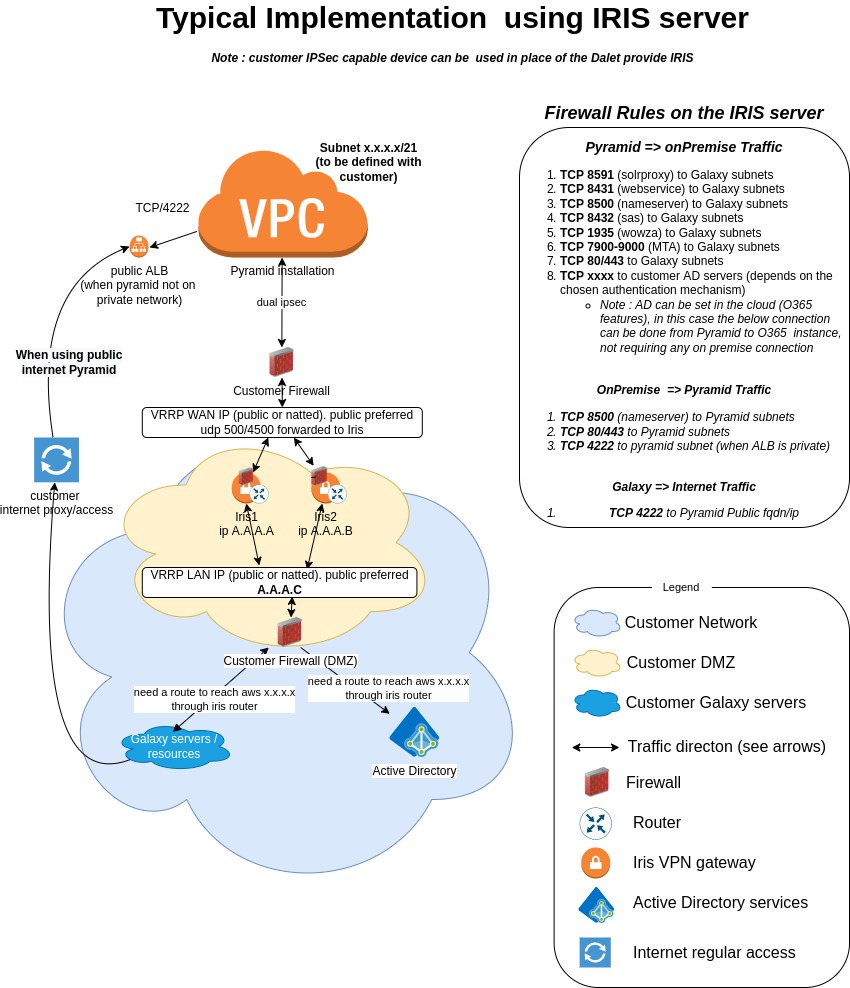
Technical Requirements for Iris implementation
Those requirements are for typical usage with connection requirement of 1 Gbps.
- Iris can be composed of 1 or 2 servers (when High-Availability is requested).
- Hardware:
- 2 vCPU (model shall not be older than 5 years).
- 4 GB Memory
- 50 GB HDD (SSD is preferred)
- Software:
- Ubuntu 22.04 LTS, server. Minimal installation with SSH support. A Dalet-issued OVA images can be provided.
- Connectivity:
- The Iris servers (when deployed for HA) must be in the same L2 network to leverage VRRP and VIP feasibility.
- Iris supports static, BGP & OSPF routing.
- Iris requires a minimum 1 Gbps LAN connection.
- Iris requires WAN connection (ingress+egress) with the targeted usage bandwith (the bandwidth can be shared between the 2 servers, Iris running in active/passive mode).
- Iris servers MUST be Internet facing (ie: have a public IP).
- Public IP support through NAT is poissible but requires extra configuration steps.
- When HA is expected: Iris requires a floatting WAN Virtual IP (ie: if not behind a NAT, Iris will require 3 public IPs) and a LAN Virtual IP.
- If behind NAT, Iris' outgoing public IP shall always remain the same (no IP pool balancing).

Comments
0 comments
Please sign in to leave a comment.